MITRE ATT&CK vs. NIST CSF
What is the MITRE ATT&CK framework, how does it relate to NIST CSF, how can they be used together, and how does Verve Industrial assist with MITRE ATT&CK?
Learn MoreSubscribe to stay in the loop with the latest OT cyber security best practices.
This article addresses these questions:
The MITRE ATT&CK® framework is a publicly available knowledge base of observed adversary behaviors categorized into specific tactics and techniques across an adversary’s attack lifecycle. MITRE ATT&CK provides a taxonomy or vocabulary when discussing cyber security incidents or threats. And most importantly, it is an evolving knowledge base that gathers the latest intelligence from the community and updates its models over time.
MITRE ATT&CK (MITRE Adversarial Tactics, Techniques, and Common Knowledge)
The MITRE ATT&CK framework was released by the MITRE Corporation in 2015, born of insights from an internal research project (notably Blake Strom’s red team) known as the Fort Meade eXperiment (FMX).
The MITRE Corporation was founded in 1958, an off-shoot of the MIT Lincoln Laboratory. MITRE is a non-profit and oversees federally funded research and development centers (FFRDCs, such as Fermilab) on account of various US Government agencies, including DoD and Homeland Security.
Tactics: The different tactics used by an adversary during an attack can be thought of as a sequence of events, almost like a movie. Each tactic represents a goal that the adversary is trying to achieve, and leads to the next goal in the sequence.
Techniques: Techniques refer to the specific tools, processes, and steps that the adversary takes to achieve a specific tactic.
The “Persistence” tactic pertains to the adversary’s objective to maintain system access during restarts, changed credentials, and other interruptions. MITRE ATT&CK identifies 19 different techniques used to accomplish this purpose – from Account Manipulation (such as modifying account credentials or permission groups, performing iterative password updates to bypass password duration policies, etc.) to Shortcut Modification (create or edit shortcuts during system boot or user login to reference other programs that will be opened or executed). These are techniques that maintain connectivity in the system.
The image below shows the matrix of tactics and techniques of the MITRE ATT&CK for Enterprise framework.
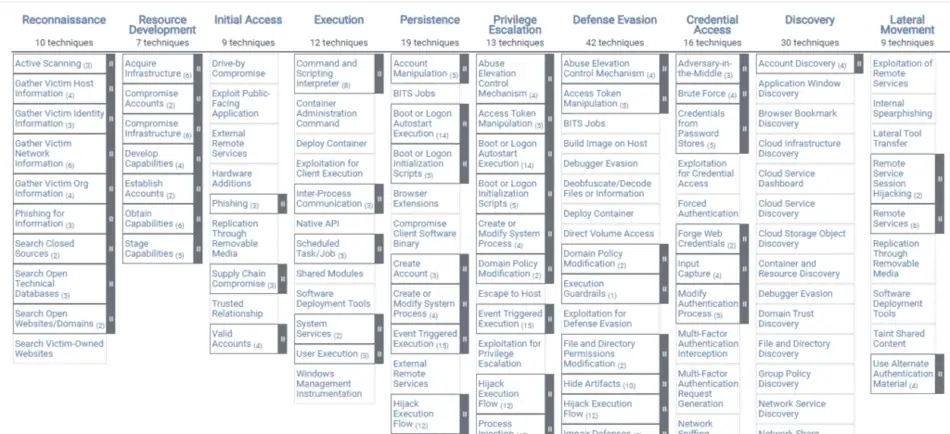
There are 14 Tactics in the Enterprise framework:
In each of these 14 tactics, MITRE describes the various techniques that adversaries can use to achieve the tactical objective. In total, in ATT&CK for Enterprise. there are 188 different techniques, which are not all unique to one tactic. Within each of these techniques, MITRE also provides a robust set of detailed information. For instance, for the technique External Remote Services found within the Initial Access tactic, MITRE provides a drill-down option to learn more about:

As you can see from the list of tactics, there is a logical sequence to these tactics. However, these do not necessarily happen in order, nor does each attack have to use each of these techniques.
The MITRE ATT&CK® framework has rightfully gained widespread awareness and attention within cyber security teams around the world. Its structuring of adversary behaviors into different steps based on real-world observations is a significant step forward for defenders of the world’s systems.
However, organizations are also familiar with or leveraging other frameworks such as those from NIST (CSF, 800, etc.), the Cyber Kill Chain introduced by Lockheed Martin, or in industrial organizations IEC/ISA 62443, etc.
Questions often arise about what exactly MITRE ATT&CK is, how to best use it, what is the difference between the “MITRE ATT&CK Enterprise” framework and the “MITRE ATT&CK ICS” framework, and how it relates to other frameworks an organization is using. Also see: How to leverage MITRE ATT&CK in conjunction with the Verve Security Center.
One question that often arises when an organization looks at MITRE ATT&CK is how it compares to the “Cyber Kill Chain®” introduced by Lockheed Martin. (http://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html) The “Kill Chain” is taken from the military environment that described the structure of an attack including the identification of the target, moving assets to the target, beginning the attack, and completion or destruction of the target. Lockheed adapted this concept to the cyber world, introducing the “cyber” kill chain.

As you can see, the two frameworks have similarities in that they both have steps in an attack and even use some of the same terms such as reconnaissance.
But there are two differences between MITRE ATT&CK® and the Cyber Kill Chain®. First, the latter is designed to help defenders “break” the chain. If the chain is broken, the attack is defended at that point. So it is a true sequence, whereas MITRE is a series of tactics which may or may not occur in order and may stop at any time but yet achieve that objective. Second, MITRE ATT&CK is at a much more detailed level of granularity provided by the techniques. As MITRE says in its FAQ:
ATT&CK and the Cyber Kill Chain are complementary. ATT&CK sits at a lower level of definition to describe adversary behavior than the Cyber Kill Chain. ATT&CK Tactics are unordered and may not all occur in a single intrusion because adversary tactical goals change throughout an operation, whereas the Cyber Kill Chain uses ordered phases to describe high-level adversary objectives.”
The MITRE ATT&CK framework is quite exhaustive and will be most useful to those knowledgeable and well-versed in cyber security.
Although many look at ATT&CK as a detection tool, in fact, it has a much broader set of use cases, and most are not about real-time monitoring and detection. There are eight broad use cases:
The framework, since it is based on real-world observations, allows an organization to develop potential scenarios of how attackers might attempt to compromise and impact their systems.
By studying the scenarios, an organization can model how its current defenses would hold up against the techniques described in the adversary scenarios developed. Importantly, this is about MUCH MORE than simply detection. It includes backup and restore, vulnerability and patch management, updated Anti-malware tools, etc.
The scenarios can assist red-teams and teams creating table-top exercises to build real world attack patterns for the defenders to evaluate against. This can also include the evaluation of the maturity of the organization’s SOC as to whether they can identify the techniques as they are used.
Threat hunting and monitoring teams can use the framework to ensure that their telemetry and analysis can identify the various techniques and how they link together.
By providing the real-world examples and data about tactics and techniques, MITRE enables incident response teams to logically work through potential techniques once an incident is reported. While adversaries may use new and unseen techniques, the baseline of those described in the framework can accelerate response and remediation.
Defending against the range of techniques in the ATT&CK framework requires a range of tooling and telemetry. The key to effective defense, however, is integrating this defense information into a common database so that organization can determine its protections across the range of tactics the adversary may desire.
The depth of information provided by MITRE as part of the framework content can significantly aid threat intelligence teams by providing depth and context of how that intel may display in the real-world environment.
The framework provides a common taxonomy to defenders across an organization as well as a way to describe threats to other stakeholders. This common taxonomy is enabled by the widespread awareness of the framework.
MITRE ATT&CK now has three different iterations:
Discusses the elements that are present in traditional Information Technology (IT) attacks and scenarios. It is also broken down by operating system (e.g., Windows) and a subsection devoted to cloud.
Discusses the elements that are present in Operational Technology (OT) attacks and scenarios. Unfortunately, it is separate from Enterprise’s ATT&CK framework, but because of the convergent nature of IT & OT, elements can and will overlap.
Discusses the unique adversarial behavior found when attacking iOS, Android, etc.
What is MITRE ATT&CK ICS framework? It is a knowledge base that describes the actions an adversary may use while operating in an industrial control system (ICS) environment. It focuses on post-compromise behaviors in specifically focused on environments where systems have an impact on the physical world and can risk health, safety, environmental impact, etc. It provides an overview of the tactics and techniques that are more likely to be present in OT/ICS environments and attempts to tailor cyber security to communities with very different priorities than the audience intended for the Enterprise ATT&CK matrix.
Although ICS systems leverage many technologies common to the Enterprise such as Windows and Linux servers and workstations, they also include many unique devices not found at the Enterprise level. In addition, these systems control physical processes and therefore the impact an adversary may aspire to can have very different consequences than those envisioned in the ATT&CK for Enterprise framework.
Therefore, MITRE undertook to develop a specific framework for these environments. It is heavily focused on what is referred to as “Level 0-2 of the Purdue Model”. For those readers unfamiliar with the Purdue model, it basically describes system levels within ICS or “Operating Technology” environments. Levels 0-2 are those closest to the physical operating sensors, valves, etc. These devices often operate with proprietary, embedded firmware and conduct physical operations to open and close connections or increase temperature or pressure. As a result, the traditional Enterprise techniques did not encompass the type of adversary behavior for these environments.
MITRE ATT&CK ICS is intended to focus on the following types of systems:
The below matrix demonstrates the MITRE ATT&CK for ICS.
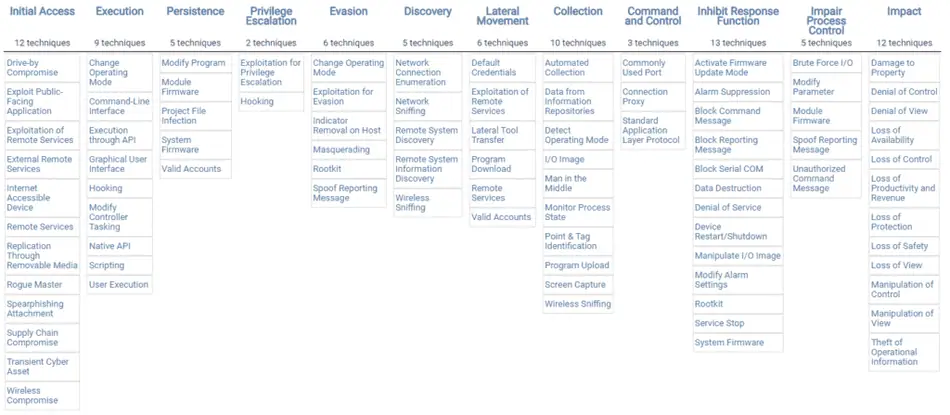
What a close reader will notice is that the tactics are very similar to those found in Enterprise, which is a good thing as industrial organizations will need to use both frameworks to cover their entire environment. In ICS, MITRE excludes the two “Pre-ATT&CK” elements of Reconnaissance and Resource Collection as they are covered in Pre-ATT&CK. However, the framework for ICS excludes two tactics from Enterprise and adds two additional ones:
The result is 11 Tactics in MITRE ATT&CK for ICS.
Although MITRE ATT&CK for ICS appears relatively similar at the tactic level, the difference, in the techniques is significant. The techniques, even for those tactics that also appear in the Enterprise framework, focus specifically on how an adversary would seek to impact an operating environment. Certainly adding the impairment and inhibiting of process control tactics is an important addition, but the shift in the techniques is where the “action” is. For instance, in the Execution tactic, the ICS framework includes items such as:
And while adding items like the above, the framework for ICS excludes Execution tactics found in Enterprise, such as:
But many techniques remain with slight adjustments such as the Scripting technique found in the Execution tactic where the potential scripts in focus in ICS may be different from the Apple scripts, etc. found in the Enterprise.
There are several other differences in the ICS framework from the Enterprise:
The use cases intended by MITRE include all the ones listed above for the Enterprise framework. In addition, however, there are two additional use cases as described in MITRE’s Philosophy Paper on the ICS framework:
One of the risks in distributing a new framework for ICS is that organizations may believe that for their OT environments, all they need is the ICS framework. This is not MITRE’s intent, nor is it appropriate. The two frameworks are intended to be used in tandem to provide a comprehensive picture of an industrial environment. As MITRE says in its ICS philosophy paper,
“The initial stages of these attacks involving IT infrastructure were able to be expressed using tactics, techniques, and procedures (TTPs) present in the ATT&CK for Enterprise knowledge base. For instance, according to Industroyer [5] or Triton [6] incident reports, IT infrastructure was leveraged solely to gain access to control systems [4]. Industroyer utilized Remote System Discovery (T1018) [7] and Network Service Scanning (T1046) [8] to map the network and find computers relevant to the attack. Adversary behavior in the later stages of these attacks, however, is out of scope for ATT&CK for Enterprise. The adversary’s targets and actions significantly differ between the Enterprise and ICS technology domains. For example, Industroyer has the capability to issue Unauthorized Command Messages (T855) [9] to change the state of electrical substation switches and circuit
breakers directly. This activity is out of scope for ATT&CK for Enterprise but is now represented as T855 [9] in ATT&CK for ICS.
ATT&CK for ICS seeks to fill this gap, adversary behavior out-of-scope of non-ICS technology domains, and address the unique concerns of the ICS domain…Due to the use of IT platforms to host critical ICS applications such as HMIs, there is some overlap between the Enterprise and ICS technology domains.”
The reality is that IT and OT are converging. ICS networks are using more and more “IT” systems – Windows, Unix, enterprise networking, virtualization, cloud, etc. As a result, it is key that organizations that have ICS networks do not forget about the Enterprise framework while protecting those industrial networks.
For example, an attacker may manage to gain access through a compromised VPN gateway, or RDP terminal server (initial access – external remote services/internet-accessible device). From that position within the network, the attacker may traverse laterally* from one system to another after deriving privileged account credentials that are often reused (Lateral movement – default credentials).
Eventually, the attacker arrives at a control room network segment by means of compromising an operator’s workstation (Initial compromise – engineering workstation compromise). The attacker deploys ransomware to disrupt operations on all vulnerable systems (Inhibit Response Function – Denial of Service) and denies process visibility to the operators, and so the process is stopped (Impact – Denial of Control/View, Productivity and Revenue).
This example is not contrived and there is a high probability this exact scenario has played out for an industrial organization’s incident response and cyber security teams to manage. As illustrated, there are elements within that scenario that encompass the verticals seen in the table header in Figure 4, as well as techniques that may belong in both IT and OT environments.
Where * is denoted, the ICS ATT&CK framework does not have a specific technique outlined, but this is easily remedied using the Enterprise framework to fill in the gaps. In this scenario, ATT&CK works well to isolate key elements when detecting, triaging, isolating, and describing a cyber incident after it occurred. But had other cyber security capabilities been used and correctly operationalized, the framework elements could have been leveraged to help prevent the organization’s impact expansion.
The organization should use the two frameworks together to provide comprehensive tactics and techniques.
As stated earlier, there are multiple use cases for the ATT&CK frameworks. In most of these, it is used to understand current defenses as well as evaluate potential incidents in a structured way based on real-world adversarial behavior. A demonstration of how MITRE ATT&CK aligns with NIST CSF is below (see whitepaper on MITRE vs. NIST).

Combining ATT&CK with NIST CSF illustrated various components to demonstrate how ATT&CK could polish an organization’s security posture. For example, ABC Corporation has:
ABC Corporation would use the ATT&CK framework to standardize attack language and enhance workflow conditional attributes that could alter the security team’s flow execution.
The MITRE ATT&CK won’t invalidate or replace investment in other cyber security frameworks NIST CSF, ISO 27001, or any other security framework, but instead acts as a multiplier when tuning security technology, policies, and procedures – especially when you have a security team in-house or external Security Operations Center. It is also useful as your organization prepares for the worst or is likely to be a frequent target, but it does not replace legislation and compliance requirements.
One of the most compelling use cases for MITRE ATT&CK is to use it to evaluate an organization’s current defenses against real-world adversaries. We have worked with industrial organizations to develop robust scenarios of attacks on their systems to evaluate how their current defenses would react in such a scenario. MITRE recognizes the advantages of a suite of defenses to stop an attack. The tactics and techniques highlight the adversary perspective that allows the defender to determine which layer of defenses will be most effective. It also recognizes there is no “one way” that a tactic can be achieved. So effective security requires a defense in depth or similar mindset.
By evaluating current tools, procedures and policies against scenarios, organizations quickly see how critical it is to have comprehensive visibility of those defenses in one place. Perhaps the biggest challenge to today’s cyber security is the range of tools and organization silos or “towers” in achieving comprehensive security. The ATT&CK framework and the scenarios it enables highlight the gaps where defenses can fall between the cracks of these tools and groups if there isn’t a common view in a single database.
Please see our whitepaper on how Verve can be leveraged with the MITRE ATT&CK framework.
What is the MITRE ATT&CK framework, how does it relate to NIST CSF, how can they be used together, and how does Verve Industrial assist with MITRE ATT&CK?
Learn MoreMake sense of the MITRE ATT&CK framework and create additional value through reporting and SIEM capabilities.
Learn MoreDownload the our whitepaper to discover the five guiding principles you should consider for your organization.
Learn More