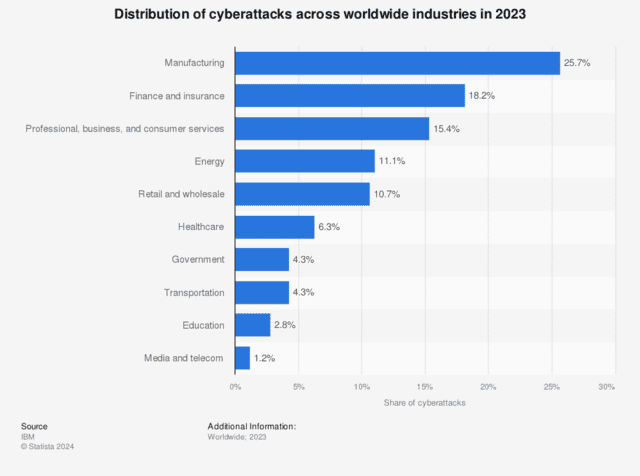
The Rising Threat to Industrial Infrastructure
In today’s hyperconnected world, the operational technology (OT) powering our industrial infrastructure has become a prime target for cyber attackers. No longer in the shadows of IT systems, OT networks and information control systems (ICS) are now squarely in the crosshairs of sophisticated threat actors.
The Regulatory Response
This surge in cyberattacks on ICS hasn’t gone unnoticed. Governments and regulatory bodies worldwide are responding with unprecedented urgency, introducing a wave of new security mandates and compliance requirements. From the United States to the Middle East, from Europe to Asia-Pacific, regulators are tightening the reins on ICS security standards, demanding more robust protection for these critical systems.
The Perfect Storm for Industrial Organizations
For industrial organizations, this rapidly evolving threat landscape and regulatory environment creates a perfect storm of challenges.
The critical question: How can companies effectively secure their OT environments while navigating this complex compliance maze?
Our Approach: Insights from 20 Years of Experience
Drawing on our 20 years of experience in helping organizations achieve and maintain compliance across various regulations, we’ve developed key insights and strategies to tackle this mounting challenge.
Subscribe to our newsletter to stay in the loop with the latest OT cyber security best practices.
Verve’s Biweekly Newsletter
Subscribe to stay in the loop with the latest OT cyber security best practices.
Fill out form below
AIR-RAID: A Framework for Understanding ICS Security Challenges
To truly grasp the multifaceted nature of today’s OT security landscape, we’ve developed the AIR-RAID framework. This mnemonic device encapsulates the key challenges faced by industrial organizations in protecting their critical infrastructure:
A – Attackers: The threat landscape is evolving rapidly, with sophisticated, profit-driven cybercriminals increasingly targeting industrial systems.
I – IT Convergence: The lines between IT and OT are blurring, necessitating the application of IT-like security capabilities in OT environments.
R – Regulation: Various regulatory bodies’ growing array of prescriptive security requirements is reshaping the compliance landscape.
R – Resource Constraints: OT teams often lack the specialized resources to manage complex cybersecurity demands.
A – Access Concerns: The rise of remote work and interconnected systems has amplified worries about unauthorized access to vulnerable ICS.
I – Insurance Pressures: Skyrocketing cyber insurance rates and stricter requirements force industrial organizations to reassess their security posture.
D – Director Scrutiny: Board-level executives increasingly focus on cybersecurity risks, demanding greater visibility and assurance.
The Interplay of Challenges
The AIR-RAID framework reveals how these factors interact and compound. The rapidly evolving threat landscape (Attackers) collides with the need to modernize security approaches (IT Convergence) in an environment of increasing oversight (Regulation and Director Scrutiny).
Meanwhile, teams must grapple with limited resources and expertise (Resource Constraints) while addressing new vulnerabilities (Access Concerns) and financial pressures (Insurance).
Navigating the Complexities
To effectively address these interconnected challenges, organizations need:
- A holistic understanding of the ICS security landscape
- The ability to view security strategies through the AIR-RAID lens
- Comprehensive approaches that protect critical infrastructure while meeting compliance requirements
In the following sections, we’ll explore practical steps to address these challenges, drawing on our extensive experience in helping companies achieve and maintain compliance in this dynamic environment.
Watch on Demand:
The Coming RAID on ICS Security
Learn how Regulators, Attackers, Insurers, and Directors (R-A-I-D) are driving rapid change in IIoT/ICS security. Discover strategies to strengthen your defenses and meet emerging demands in this critical landscape.
Five Key Steps to Successful ICS Security Compliance
Over our 20 years of experience helping companies navigate the complex world of ICS security compliance, we’ve identified five critical steps that consistently lead to success. These steps address the challenges outlined in our AIR-RAID framework and provide a roadmap for organizations looking to enhance their ICS security posture while meeting evolving regulatory requirements.
Assign Dedicated Leadership for ICS Management
Dedicated leadership for Industrial Control Systems (ICS) security management is becoming crucial as cyber threats increase and regulations tighten. Unlike IT departments with established security practices, ICS environments face unique challenges such as resource constraints, legacy systems, and distributed assets. These challenges demand a comprehensive approach to security management.
This approach, OT Systems Management (OTSM), requires more than just a designated cybersecurity coordinator. Organizations need leadership to oversee critical functions across diverse systems, including asset identification, vulnerability assessment, network monitoring, configuration compliance, and more.
Industry trends highlight this need, with over 75% of cybersecurity roles focusing on systems management. By prioritizing ICS security early and using frameworks like NERC CIP and NIST, companies build a strong foundation to meet evolving threats and regulations like TSA guidelines and NIS2 standards.
Remember, cybersecurity maturity can’t be achieved overnight. A proactive approach allows time to implement essential security elements, making full compliance more achievable in the long run.
Design OT Security with the End Goal in Mind
Designing an OT security program requires a holistic, forward-thinking approach rather than implementing individual requirements piecemeal. This lesson emerges from the experiences of early NERC CIP adopters, who often scrambled to keep up with evolving standards and implement disconnected solutions.
A holistic approach means:
- Considering your entire OT environment and its future needs
- Aligning security measures with both current and anticipated regulatory requirements
- Implementing foundational tools and processes that can adapt and scale
Organizations create a cohesive security roadmap by using a framework like NIST CSF, IEC 62443, or CMMC as a guide. This strategy allows for the selection of tools and processes that offer broad, future-ready capabilities—from patching and vulnerability management to user access control.
Remember, the goal is to comply with today’s standards while building a resilient security posture that can evolve with the threat landscape and regulatory environment. A holistic, well-planned approach now prevents costly overhauls and security gaps in the future.
Employ Global, Vendor-Agnostic Security and Compliance
IT/OT environments present unique security compliance challenges due to their diverse and distributed nature. These systems often incorporate equipment from multiple vendors (like GE, Emerson, and Siemens) and can span vast geographic areas or complex local networks.
This diversity creates significant hurdles:
- Vendor-specific security procedures
- Multiple security “stacks” within single facilities
- Limited visibility across numerous locations
As a result, tracking compliance and monitoring security becomes increasingly complex and costly.
To address these challenges, forward-thinking organizations are adopting vendor-agnostic, consolidated solutions. By centralizing security and compliance information into global databases, companies gain:
- Comprehensive visibility across all assets
- Streamlined reporting and monitoring
- More efficient and cost-effective compliance management
This centralized approach is crucial for maintaining sustainable, up-to-date compliance in the complex OT landscape, helping organizations avoid spiraling costs and compliance gaps.
Enable Efficient Local Actions for IT/OT Security
Effective OT security compliance goes beyond passive monitoring. It requires active measures like patch management, software updates, and user account control. However, these actions can potentially disrupt critical operations in OT environments if not carefully managed.
The solution lies in a balanced approach:
- Centralize security strategy: Design security actions and policies at a global level.
- Distribute to local operations: Send approved actions to site-specific teams.
- Execute locally: Allow on-site operators who best understand their systems to control the final implementation.
This “Think Global, Act Local” approach enables organizations to maintain strong security while respecting the unique needs of each OT environment. It allows for necessary security actions without compromising operational safety, striking a crucial balance between IT security norms and OT operational realities.
Build a Talent Pipeline or Outsource Key OT Skills
Addressing the ‘Resource Constraints’ challenge requires a strategic approach to talent management. Organizations should either:
- Develop a robust internal talent pipeline, including recruitment, training, and retention strategies
- Consider outsourcing if unable to sustain an internal development program
This step ensures that organizations have access to the specialized skills required for effective OT security and compliance management.
Implementing these five key steps provides organizations a framework for addressing the challenges outlined in the AIR-RAID model, helping to create a more secure, compliant, and resilient OT environment.
Securing the Future of Industrial Operations
The landscape of OT security is undergoing a seismic shift. The convergence of sophisticated cyber threats, evolving regulatory requirements, and operational complexities creates a challenging environment for industrial organizations. However, with challenges come opportunities – opportunities to strengthen your security posture, streamline compliance efforts, and build resilience into your OT infrastructure.
The key to success? Proactive preparation. By building a strong, adaptable foundation now, you’ll be better equipped to face future threats and regulatory changes.
Ready to secure your industrial operations for the future?
Let's navigate the evolving landscape of OT security together, with confidence.