ISA 62443-3-2 standard accessible to industrial companies for automation, control systems cybersecurity
The International Society of Automation (ISA) and the ISA Global Cybersecurity Alliance (ISAGCA) have released a white paper that provides an overview of the ISA 62443-3-2 standard. It also highlights some of the methodologies that can be used to assist the execution of the industrial automation control system (IACS) cybersecurity risk assessment work process requirements.
The white paper, titled ‘Leveraging ISA 62443-3-2 For IACS Risk Assessment and Risk-Related Strategies,’ lists a summary of some of the methodologies that can be used to assist the execution of the IACS cybersecurity risk assessment work process requirements, detailed in the standard.
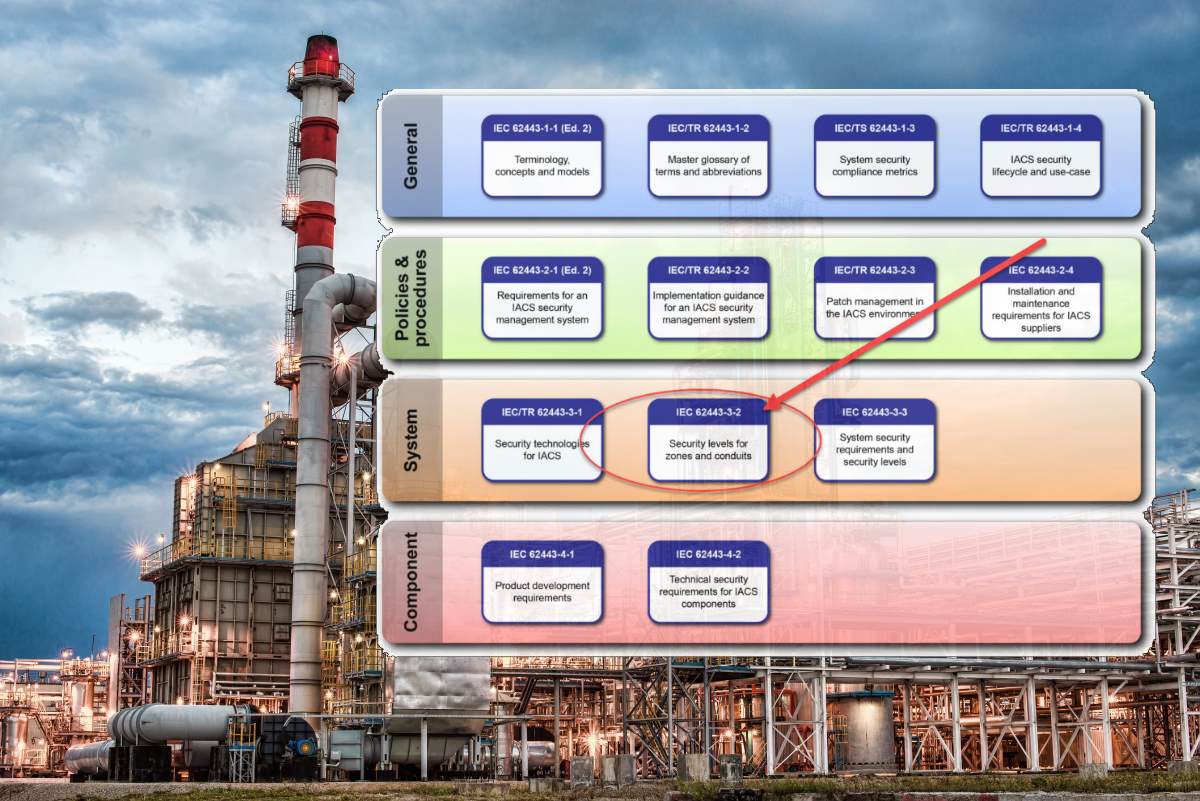
Released in February last year, the ISA 62443-3-2 standard can be purchased either from the ISA or the International Electrotechnical Commission (IEC). The benefits of using a risk-based standards approach include reducing the likelihood of a successful cyberattack, using a common set of requirements among stakeholders, providing security throughout the lifecycle, and a reduction in overall lifecycle cost.
The ISA 62443-3-2 standard sets down for industrial companies, those mainly involved in aerospace, lumber production, tools, defense, construction, waste management, cement, and metal fabrication among many others, to identify the System under Consideration (SuC), perform an initial cyber risk assessment, partition the SuC into zones and conduits, carry out a detailed level cyber risk assessment, and document update using cybersecurity requirements for detailed design.
The ISA 62443-3-2 standard provides requirements to establish a work process for cybersecurity risk assessment that can be integrated with an existing risk assessment program and represents recognized and generally accepted good engineering practice (RAGAGEP). The benefits of using this standard include reducing the likelihood of a successful cyberattack, the use of a common set of requirements among stakeholders, security throughout the lifecycle, and a reduction in overall lifecycle cost.
Prior to the initial cybersecurity risk assessment, the SuC perimeter and access points should be identified and documented, according to the white paper. It is important to recognize that when defining the SuC, the equipment ranging from field sensors and final elements all the way through to the overlapping interface with information technology (IT) within the demilitarized zone (DMZ) should be considered. In the event that the industrial internet of things (IIoT) or the cloud are used to perform functions within the operational technology (OT) levels, they would necessarily be included as well, it added.
“ISAGCA’s mission is to enable and accelerate adoption of cybersecurity practices for all stakeholder groups based on the ISA/IEC 62443 family of automation cybersecurity standards,” commented Andre Ristaino, ISAGCA Managing Director. “Our member companies are working in collaboration with one another, industry partners, and regulatory/legislative bodies to secure automation that affects our everyday lives.”
Based on the understanding that IACS security is a matter of risk management. IACS customizes risk to an organization depending on the relevant threat, risk exposure, the likelihood of an event, inherent vulnerabilities, and consequences of compromise.
“Each organization that owns and operates an IACS has its own tolerance for risk, and organizations are required to provide inputs used to assess the risk of a particular IACS, Ron Brash, director of cybersecurity insights at Verve Industrial, wrote in a company blog post. “Based on those inputs, ISA/IEC 62443-3-2 can help when engineering a solution by guiding the identification/application of security countermeasures to reduce that risk to tolerable levels with respect to defined security levels, zones, conduits, and other security fundamentals.”
The ISA 62443-3-2 standard is based on the understanding that IACS security is a matter of risk management. Each IACS presents a different risk to an organization depending upon the threats it is exposed to, the likelihood of those threats arising, the inherent vulnerabilities in the system, and the consequences if the system were to be compromised. Further, each organization that owns and operates an IACS has its own tolerance for risk.
“For these reasons, ISA/IEC 62443-3-2 will define a set of engineering measures to guide organizations through the process of assessing the risk of a particular IACS and identifying and applying security countermeasures to reduce that risk to tolerable levels,” wrote cybersecurity expert Anastasios Arampatzis in a blog post for Tripwire.
Vendors have also moved towards creating technologies that cover the ISA 62443-3-2 standard. For instance, aeCyberSolutions announced in April that its aeCyberPHA Facilitation Suite for industrial asset owners looking to self-perform, maintain, and manage cyber PHA (process hazards analysis) cyber-safety risk assessments. The suite includes an all-in-one package of the tools, training, and guidance needed to successfully lead an ISA/IEC 62443-3-2 compliant risk assessment per the proven cyber PHA methodology.
Industrial cybersecurity has repeatedly been hit in the last few months with a spate of ransomware and other cybersecurity incidents, often disrupting operations at industrial units and the critical infrastructure segments, including water plants and fuel pipeline operations.










